As terrorism research is moving from a situation with data scarcity to abundance, we need to reassess our methods. The most common approach to measuring terrorism has been to look at launched attacks and count their incidence. This intuitively seems like the best way to do it, and yet it is highly problematic. The reason is that attacks constitute the “tip of the iceberg” (Crenshaw and Lafree, 2017), i.e. what is left after security services have done their job at foiling attack plots.
Analyses that only include attack data, therefore, risk misrepresenting both the scale and nature of terrorism. In this keynote I will talk about the value-added of including foiled plots in terrorism research, what we can learn from studying foiled plots, the challenges of working with such data, and what could go wrong with the analysis if we do not include them. Last I will touch upon some implications for research and policy.
Why am suited to talk about this?
Back in 2003, I became a research assistant for Brynjar Lia, then leader of the terrorism research project at the Norwegian Defence Research Establishment (FFI). Brynjar tasked me with mapping and making sense of the jihadi threat to Europe. He gave me a file containing a number of newspaper articles about various activities in Europe believed to be linked to Bin Laden’s network. He also equipped me with an FFI report written as early as 2000 which provided a detailed analysis of a series of attacks in France by the Algerian Islamist terrorist group GIA in the mid-1990s. Brynjar had a “gut feeling” (a highly undervalued quality in researchers) that something was brewing in Europe. I was the lowest rung on the project’s ladder with no other responsibilities apart from collecting and systemizing sources on jihadism in Europe. This gave me the opportunity and time (to an extent I would never experience again) to drill in on this particular topic.
Most of the articles in the original file were about propaganda, recruitment, money laundering, and weapons smuggling. These were fussy activities which seemed geared toward supporting jihadis in conflict zones. As my mission was to look at the potential terrorist threat to Europe I focused on a few articles which dealt with attack plots that had been foiled by counterterrorism. There was quite a lot of information on them, and so I decided to treat these plots as the most tangible signs that a threat was emerging, and thus my main units of analysis. I studied them intensively, using media sources and court documents mainly. In some cases I also had the chance to meet with counterterrorism officials who had investigated jihadist terrorist cells operating in Europe.
I began to build a chronology of attack plots in which I wrote down thick descriptions of each case, including the background of the perpetrators, what they had planned to do and what they had done to prepare. Then I selected a few cases that were particularly well documented and studied them in great detail. Perhaps somewhat sadly, at one point during those days, I was far better at remembering names of European jihadis than acquaintances from my work and personal life. This all resulted in my MA, which was a study about terrorism in Europe but without addressing one single attack. It was a study of non-events. The month I handed it in to the political science department at the University of Oslo (UiO), jihadis bombed commuter trains in Madrid in the hitherto deadliest attack by Islamist militants in Europe. From then on, my chronology became one of foiled plots as well as attacks, and the basis for several reports, articles and a 2015 book on the history of European jihadism. Over the years, I have become increasingly interested in the relationship between foiled plots and attacks and what it means methodologically for how we gauge a threat’s scope and nature. I will share some of my thoughts on the matter in the following, but first,
What is a terrorist plot?
A terrorist plot can be challenging to define. The concept is used to describe various phenomena ranging from an expressed idea or vague intention to conduct an attack, to very concrete acts of preparation and implementation. In my work I use “terrorist plots” overall to denote both attacks and concrete plans thereof. I consider a plot launched when perpetrators reach the stage where they physically attempt to hurt the target. I talk about foiled plots when plans derail for different reasons before the perpetrator can implement. As I will come back to, this mostly happens because security services intervene, but sometimes a plot derails because the perpetrator makes mistakes (sometimes very amateurish ones) or has a change of heart.
In my chronology of European jihadism I include all attacks, and then I include foiled plots when there is sound empirical evidence of a jihadi intention, a specified target (or a clear statement by authorities that an attack was in the making), and material steps toward implementation (bombs, guns, reconnaissance video, maps). Because the information about foiled plots can be scarce, or dubious, and varies from case to case and between countries, many qualitative assessments are necessary when including or excluding them from a dataset. This leads me to the next question: how can we study and make sense of the attacks that did not happen?
How can we study foiled plots?
 The first rule of including foiled plots as units of analysis in terrorism research is to do it with a solid dose of skepticism. Terrorism is a secret activity and the source of the information that reaches the public domain is usually leaks from early phases of investigations, or intelligence officials. It can be in the interest of states to manipulate information to justify countermeasures, or be able to disrupt an extremist milieu that might be considering attacks, but has yet to take the plans further. This problem is probably not too huge in democracies though, as there are institutionalized checks on what security services can, and cannot do. My approach is to gather as much information as possible from open sources first, using any conceivable source (even shady ones, such as extremist websites, or tabloids). Each source needs to be assessed separately first and then triangulated if possible.
The first rule of including foiled plots as units of analysis in terrorism research is to do it with a solid dose of skepticism. Terrorism is a secret activity and the source of the information that reaches the public domain is usually leaks from early phases of investigations, or intelligence officials. It can be in the interest of states to manipulate information to justify countermeasures, or be able to disrupt an extremist milieu that might be considering attacks, but has yet to take the plans further. This problem is probably not too huge in democracies though, as there are institutionalized checks on what security services can, and cannot do. My approach is to gather as much information as possible from open sources first, using any conceivable source (even shady ones, such as extremist websites, or tabloids). Each source needs to be assessed separately first and then triangulated if possible.
In my work, I have on occasions experienced to find more accurate information in a tabloid newspaper than in reputed international media outlets, so it all comes down to the journalist and the sources on which the article is based. Still, although media is a key tool (especially local newspapers), if you want to go deeper and study the inner workings of terrorist networks you need to read police documents, court records, and interview investigators. Then, if the situation allows you should use any opportunity to talk to the terrorists themselves, preferably after they stopped being terrorists (for obvious reasons).
One important lesson learned is that there is an information cycle, implying that many details on plots surface when they are first reported. Then everything goes a bit dark until the trial when the case suddenly can appear quite different than it did at the outset. So when we include foiled plots, we should strive for a thick plot description from the very start and update continuously as new information surfaces. To make sure not to over-report plot activity I invented a system where I exclude plots in which information about perpetrator, target, and preparation is too vague. When all elements are well-documented it is a sure thing (category 1), when two elements are well-documented it should be included as a category 2 case, but if there are uncertainties on all three (category 3) I do not want the plot as a unit of analysis. Building a plot dataset is terribly labor-intensive, but as I shall argue well worth the trouble because we can learn a lot from studying foiled plots.
What then can we learn from foiled plots?
First of all, because I am studying jihadism, and its adherents have this unfortunate tendency to commit suicide attacks, studying a foiled plot means that the perpetrator usually is alive and can talk to interrogators or judges about their motives. As I will come back to it is also in the nature of things that foiled plots involve groups, cells, or networks composed of multiple perpetrators interacting. This allows for studying the inner workings and social dynamics of violent subcultures. Investigations of foiled plots have revealed highly interesting details about intra-group dynamics, the camaraderie among cell members, conflicts between them (sometimes over very mundane matters), rivalry over leadership in the group, what they do for recreation, or rituals (the oddest being a radical preacher in Holland who reportedly fed cell member breastmilk from his wife to symbolize they were like sons to him).
Exactly because foiled plots tend to be group phenomena, they are a window to types of information that can help us distinguish between different roles in a cell and how the motives vary among people involved. In my work, I came up with typology of cell members which functioned as a tool enabling me to distinguish between different pathways to terrorism: the ideological track associated with the entrepreneur and his protégé, the personal misfortunes associated with the misfits and the social pull factors associated with the drifters. Furthermore foiled plots can teach us much about the transnational character of terrorism because the very process of foiling a plot involves mapping the network. With attacks this is harder. The perpetrator can be dead or does everything possible to protect the network, if there is one at all. From my experience with studying foiled jihadist plots in Europe I have learned that they more often than not involve network interactions, offline and online, within Europe, across the Atlantic and more commonly to conflict zones of the Middle East.
In addition to the inner dynamics of cells and the network dimension, foiled plots contain valuable information on tactics, targets, and weapons. A few years ago, colleagues and I started to include foiled plots in analyses of modus operandi. What we found was that certain tactics and weapons were more prevalent in plots that were foiled compared to the attacks that were launched. This brings me to the next point of what could go wrong if we measure the scope and nature of terrorism based on attacks only.
What could go wrong if we do not include foiled plots?
Based on the observation that foiled plots outnumber attacks and that the foiled ones differ in characteristics from launched attacks, there is a considerable risk to misrepresent terrorism if we look at attack data only. The launched attacks may not be representative – neither of the threat level as such nor things like cell configurations or trends in tactics. This is actually quite serious when we know that many common assumptions about terrorism rest on databases and research that do not include foiled plots.
As a “plot researcher,” I often feel at odds with how the general public perceives the overall threat level, especially in years when many plots get stopped by security services, or in years when security services intercept plots that would have been large-scale and very deadly if they had been implemented. It can sometimes be a frustrating experience for a jihadism “plot researcher,” to read opinion pieces and popular research invoking attack data from the Global Terrorism Database or Europol’s yearly T-Sat report to claim that separatists pose a greater threat than jihadists in Europe, or that right-wing terrorists are just as dangerous as jihadis. The jihadi threat in Europe looks quite different if we include the foiled plots. Let me just mention some examples of how attack data can misrepresent patterns of European jihadism and how the inclusion of foiled plots can give a better understanding of the threat.
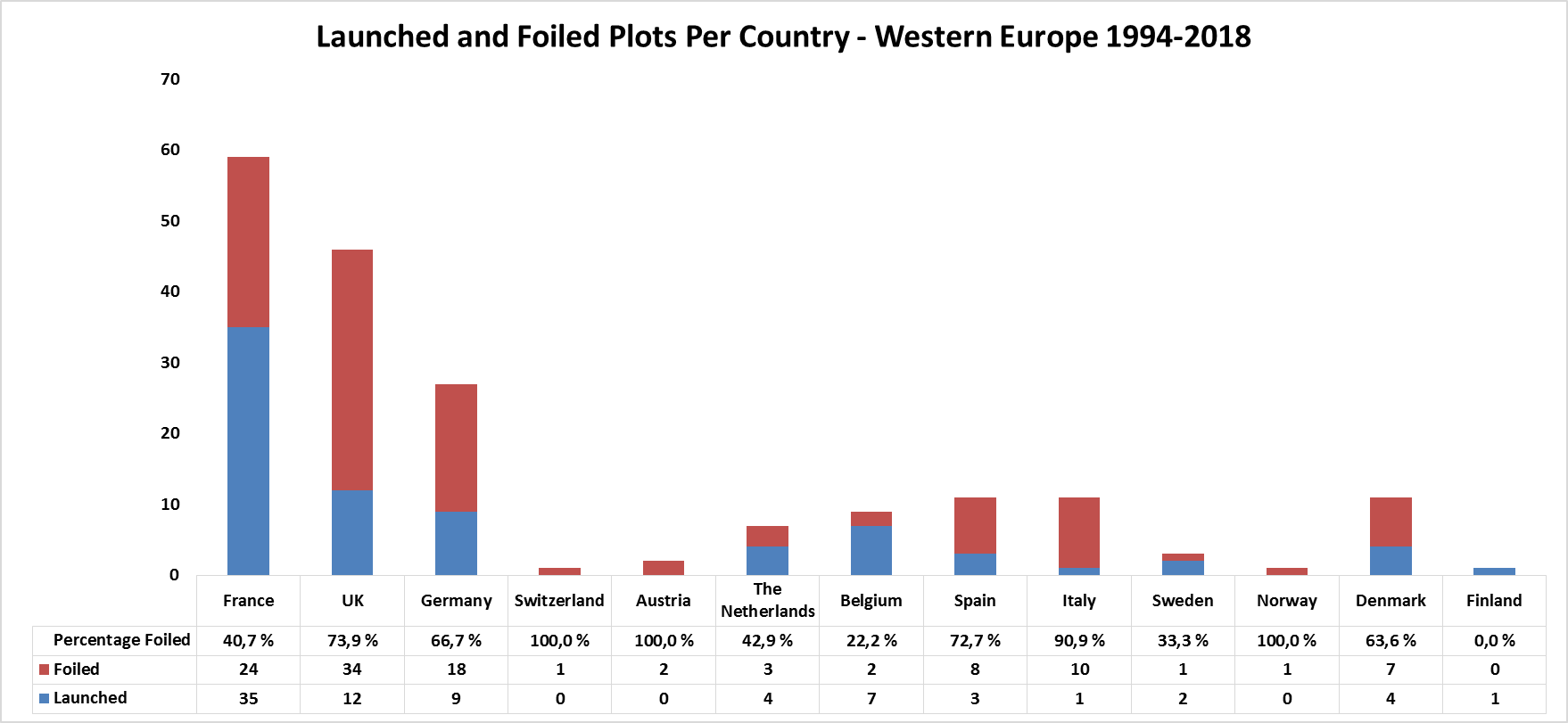
To begin with, the overall threat can be misrepresented by not including foiled plots. In 2018, attacks by jihadis fell by some 50 % in Europe compared to the high numbers seen in 2016 and 2017. This led many to believe that the threat is disappearing with the fall of IS and that we now can concentrate on other things. However, if we include the foiled plots in the assessment we see that total attack activity in 2018 was higher than any given year before 2015 (higher than in the 2000s when al-Qaida was targeting Europe). Adding to this, some of the foiled plots in 2018 were large-scale, for example the group of seven arrested in Holland for plotting to attack a public event with automatic guns grenades and explosives, while setting off a car bomb at another location.
Second, the relative threat posed by different actors can be misrepresented if we only consider attacks. Yearly reports by Europol have been invoked to show, for example, that separatists execute far more terrorist attacks than jihadis in Europe. Such analyses do not take into account that jihadism, in contrast to most cases of separatism, is a transnational threat and one which is more likely to cause mass-casualty attacks. More importantly such analyses do not take into account that jihadism has been the main concern for western security services after 9/11 and that this is a major reason why many and potentially very deadly attacks have been foiled. One important example is the 2006 “Airliner plot” to down multiple trans-Atlantic jets departing from the UK. This is an incident which is not reported in databases such as GTD. If implemented, it could have killed more people than have been killed by jihadis in Europe all together since the 1990s and dramatically altered the threat analysis of European jihadism.
Third, a focus on attacks can misrepresent trends in how terrorists organize and operate. Studies of European jihadism, which have looked at both attack and plot data show that certain types of modus operandi and cell configurations are underrepresented in attack data. The attacks that get executed tend to be small attacks by an individual with simple weapons, whereas counterterrorism disproportionally foils complex attacks by groups and larger networks that seek to employ bombs or combine different weapons. In 2016, an FFI study which looked at both launched and foiled attacks by European jihadis found that “Single-actor terrorists go undetected in 57 % of the cases while groups go undetected in only 26 % of the cases”.
Fifth, by only studying launched attacks we might misrepresent aspects such as the involvement of foreign fighters. For example, when we look at attacks recorded in FFI data by followers of Islamic State in Europe in 2014-17 some 15 % (six out of 39 attacks) involved (at least one) foreign fighter. If we include foiled plots there was at least one foreign fighter in as many as 20 out of 81 cases, - nearly 25 %.
Sixth, if we do not consider plot foiling, we risk misrepresenting the relative threat to different countries. This can, in turn, lead to problematic inferences about causal connections. Looking at attacks only, France stands out as the main target for jihadi terrorism in Europe, and we intuitively look for explanations specific to France (for example its failure to integrate Muslim immigrants or its way of trying to assimilate them). However, if we look at data which include foiled plots we see that France is not so special after all. The UK also experiences a very high frequency of plots, the difference being that the Brits foil more plots than the French (74 % vs 41 %). This is interesting in terms of generating hypotheses about what causes the threat, especially since the UK has a very different approach to integration than France, relying on multi-culturalism rather than assimilation.
So what does this mean for research and policy?
The tendency for plots to derail, mostly because of counterterrorism, varies between European countries and also between regions, and over time. In a forthcoming study, another experienced “plot researcher,” Thomas Hegghammer and I, highlight that this constitutes a measurement problem for terrorism research (for jihadism in the West and perhaps beyond). In the article, we concentrate on jihadism in the West and compare widely used datasets which only includes attacks (attack datasets) with datasets that also includes foiled plots (plot datasets).
In order to provide a measurement of how much of the total attack-geared activity gets underreported in attack datasets, we compare GTD attack data with plot datasets for Europe and the US (only datasets which cover 15 years or more). Because the datasets differ on inclusion criteria and coding we made some technical adjustments such as aggregating sequential attacks, to make comparison possible.
We define the underreporting as “plot attrition” and it represents the “ice-berg” in the aforementioned “tip-of the iceberg” metaphor. We find that average yearly plot attrition is high, at about 50 % for Europe and about 75 % for the US, meaning that there is roughly two foiled plot per attack in Europe per year and three in the US. Because plot datasets are rare for non-western countries and non-jihadi actors we cannot say much about generalizability at this point, but there are indications that the attrition is substantial for other actors and in other regions. Several studies indicate that quite a few rightwing plots get stopped, albeit not as many as in the jihadi domain. Israel reported high plot attrition for Palestinian suicide bombings (70 %) in the first half of the 2000s. A forthcoming FFI study of jihadi attack activity in Jordan shows that the security apparatus in that country foils nearly 85 % of attack plots.
In the forthcoming article, we discuss some intuitive hypotheses as to why plot attrition varies, but we have yet to reach any firm conclusions. The methodological point we want to make is that as long as plot attrition exists (we show this), is not constant (we show this), and its variation has yet to be accounted for, analyses that only invoke attack data could be based on a flawed metric.
Because much of what we think we know about terrorism is based studies using the number of attacks as the dependent variable this is of no small consequence. In cross-country studies looking at the effects of variables such as political regime, economic development, or migration, for example, findings could be misleading if we do not consider counterterrorism as an intervening variable.
As research influences public debates, which in turn influence political decisions failure to consider plot attrition could have dire effects. If, for example, decision-makers start perceiving the jihadi threat as disappearing, resources may be diverted to other pressing issues. If there is a widespread perception that jihadists only conduct small-scale attacks, counter-measures designed to abort the large-scale ones, such as the 2006 “Airliner plot” could end up be down-prioritized, even though attacks of this size are the ones that could start wars.
In research, we should look into the possibilities of building more plot datasets for jihadis in other regions than the West, and other actors, such as right-wing militants. This will enhance our ability to understand counterterrorism as a variable in terrorism research.
 Petter Nesser is a senior researcher at FFI’s Terrorism Research Group. He is a political scientist, historian and arabist, and has conducted extensive research on European jihadism for more than a decade while concentrating on why and how terrorist cells emerge, and how they operate.
Petter Nesser is a senior researcher at FFI’s Terrorism Research Group. He is a political scientist, historian and arabist, and has conducted extensive research on European jihadism for more than a decade while concentrating on why and how terrorist cells emerge, and how they operate.
.jpg)
.jpg?alt=listing)


